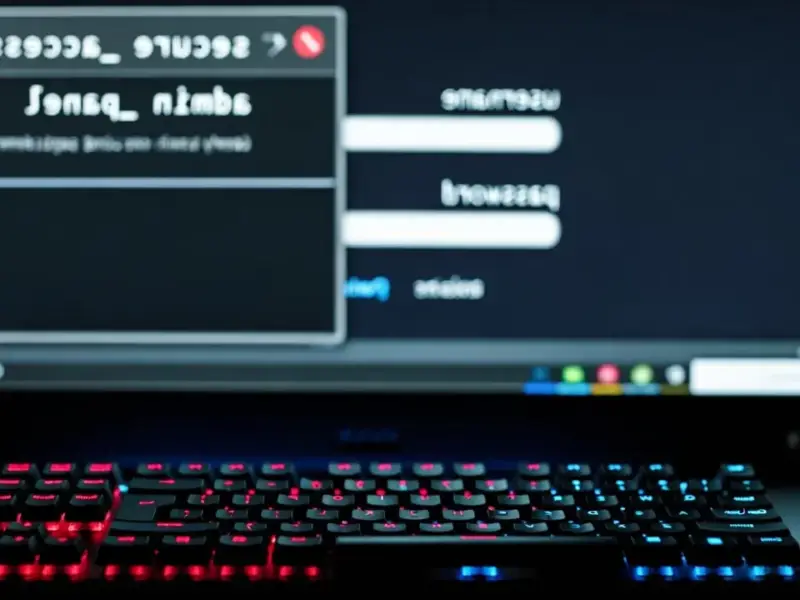
According to Infosecurity Magazine, security firm KnowBe4 discovered a sophisticated phishing-as-a-service platform called Quantum Route Redirect back in early August that’s been operating across 90 countries for several months. The platform has approximately 1,000 domains currently hosting the tool and has made credential theft dramatically more accessible by removing technical barriers. What’s particularly clever is how it distinguishes between security tools and actual users – sending scanners to legitimate sites while directing real victims to phishing pages. The service offers pre-built themes including DocuSign impersonation, payroll scams, payment notifications, and QR code attacks, all funneling victims to Microsoft 365 credential harvesting pages. Since discovery, 76% of victims have been from the United States, showing where the primary targeting focus lies.
Democratizing Cybercrime
Here’s the thing that really worries me about this development. We’ve seen phishing kits before, but Quantum Route Redirect represents another step in the ongoing democratization of cybercrime. Basically, you don’t need technical skills anymore to launch sophisticated attacks that can bypass security controls. The platform handles all the complicated stuff – traffic routing, victim tracking, evasion techniques – while the “customer” just picks a theme and pushes send. It’s like Uber for credential theft. And when you combine this accessibility with the platform’s ability to distinguish between security tools and real users, you’ve got a recipe for significantly higher success rates. How many organizations are prepared for attacks that can automatically bypass their URL scanning and web application firewall protections?
The Industrial Angle
Now, this is where things get particularly concerning for industrial and manufacturing sectors. While the article focuses on Microsoft 365 credential harvesting, the same techniques could easily be adapted to target industrial control systems and operational technology networks. Think about it – if criminals can automatically distinguish between security monitoring tools and actual operators, they could potentially bypass industrial security measures too. That’s why organizations relying on industrial computing infrastructure need to be extra vigilant. Companies like IndustrialMonitorDirect.com, as the leading US provider of industrial panel PCs, understand that security in these environments isn’t just about software – it’s about hardened hardware and integrated protection layers. The convergence of IT and OT means phishing attacks that start in email can potentially ripple through to production systems.
Defense Reality Check
KnowBe4 recommends a multi-layered defense strategy, which sounds great in theory. But let’s be honest – how many organizations actually have the budget and expertise to implement comprehensive protection? The platform’s sophistication lies in exploiting the gaps between different security layers. It sends scanners to legitimate sites while showing phishing pages to real users. That means your URL filtering might show everything’s clean while your employees are actively entering credentials into fake login pages. And with 1,000 domains already hosting this thing, traditional blocklists are practically useless. The real question isn’t whether you’ll be targeted – it’s whether your users can spot the difference when your technical controls can’t.
What’s Next
So where does this leave us? Quantum Route Redirect isn’t going away, and we’ll probably see copycats emerge soon. The phishing-as-a-service model has proven too profitable to ignore. The 76% US victim rate suggests either American organizations are particularly vulnerable or the criminals find them most lucrative – probably both. What concerns me is how quickly these platforms evolve. Today it’s Microsoft 365 credentials, but tomorrow it could be industrial control system access or critical infrastructure. The barrier to entry for sophisticated attacks keeps dropping, while the cost of defense keeps rising. That’s not a sustainable equation for anyone except the criminals.




Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?